Product
| Researcher | API | Identity Portal | Enterprise | |
|---|---|---|---|---|
| € 2.500 /Year | € 7.000 /Year | € 10.000 /Year | € 20.000 /Year | |
| Accounts | 1 user | 1 user | 1 user | Multiple users 1) |
| Target Customer | Individual | Companies | Companies | Enterprise |
| Use Case | Security Research | Integration / OEM | Advanced Security Research | Teams |
| Access to intelx.io | 🗸 | 🗸 | 🗸 | 🗸 |
| Access to identity.intelx.io | 🗙 | 🗙 | 🗸2) | 🗸2) |
| Selector Search | 200 /day | 500 /day | 500 /day | 5000+ /day |
| Phonebook Lookups | 25 /day | 100 /day | 100 /day | 2500+ /day |
| Alerts | 10 included | 100 included | 100 included | Unlimited |
| Download | 🗸 | 🗸 | 🗸 | 🗸 |
| Export (CSV, ZIP) | 25 /day | 100 /day | 100 /day | 5000 /day |
| Search API3) | Fair-use 4) | 🗸 | 🗸 | 🗸 |
| Leaks API5) | 🗙 | 🗙 | 🗸 | 🗸 |
| List Results Line-by-Line | 🗙 | 🗙 | 🗸 | 🗸 |
| Export Leaked Accounts | 🗙 | 🗙 | 🗸 | 🗸 |
| Reverse Lookup | 🗙 | 🗙 | 🗸 | 🗸 |
| Export Stealer Log | 🗙 | 🗙 | 🗸 | 🗸 |
| API Product Integration6) | 🗙 | 🗸 | 🗸 | 🗸 |
| Bulk Access | 🗙 | 🗸 | 🗸 | 🗸 |
|
|
|
|
|
| Public (not logged in) | Free (signed up) | Academia (universities & schools) | Free Trial (7-days) | |
|---|---|---|---|---|
| Accounts | 1 user | 1 user | 1 user | 1 user |
| Target Customer | ||||
| Use Case | ||||
| Access to intelx.io | 🗸 | 🗸 | 🗸 | 🗸 |
| Access to identity.intelx.io | 🗙 | 🗙 | 🗙 | 🗙 |
| Selector Search | 2 /day | 50 /day | 50 /day | 50 /day |
| Phonebook Lookups | 5 /day | 10 /day | 25 /day | 10 /day |
| Alerts | 🗙 | 🗙 | 10 included | 10 included |
| Download | 🗙 | 🗙 | 🗸 | 🗸 |
| Export (CSV, ZIP) | 🗙 | 🗙 | 2 /day | 20 /day |
| Search API | 🗙 | Fair-use 4)
| Fair-use 4)
| Fair-use 4)
| |
| Leaks API | 🗙 | 🗙 | 🗙 | 🗙 |
| List Results Line-by-Line | 🗙 | 🗙 | 🗙 | 🗙 |
| Export Leaked Accounts | 🗙 | 🗙 | 🗙 | 🗙 |
| Reverse Lookup | 🗙 | 🗙 | 🗙 | 🗙 |
| Export Stealer Log | 🗙 | 🗙 | 🗙 | 🗙 |
| API Product Integration6) | 🗙 | 🗙 | 🗙 | 🗙 |
| Bulk Access | 🗙 | 🗙 | 🗙 | Fair-use 4) |
- 5 users included. 1000 searches per day per user. Additional users may be added upon request and additional charge. Note: Enterprise accounts without a business domain will be allocated only one user account with 5000 searches.
- The Identity Portal displays results line-by-line instead of the file preview, and allows to export leaked accounts. It uses the same data set as intelx.io. Read more below.
- The Search API is the regular API used by intelx.io. It allows to search for selectors (specific search terms) and list all results.
- Fair use means that the user shall not engage in usage of the API that goes against our Terms of Service such as mass scraping.
- The Leaks API is part of the Identity Portal and separate from the Search API.
- The API, Identity Portal and Enterprise licenses allow integrating the API into third-party products. All other licenses do not grant the right to integrate our API into third-party products.
Identity Portal
The Identity Portal is a separate product. It is a different user interface that uses the same underlying data set, but processes and visualizes it differently.
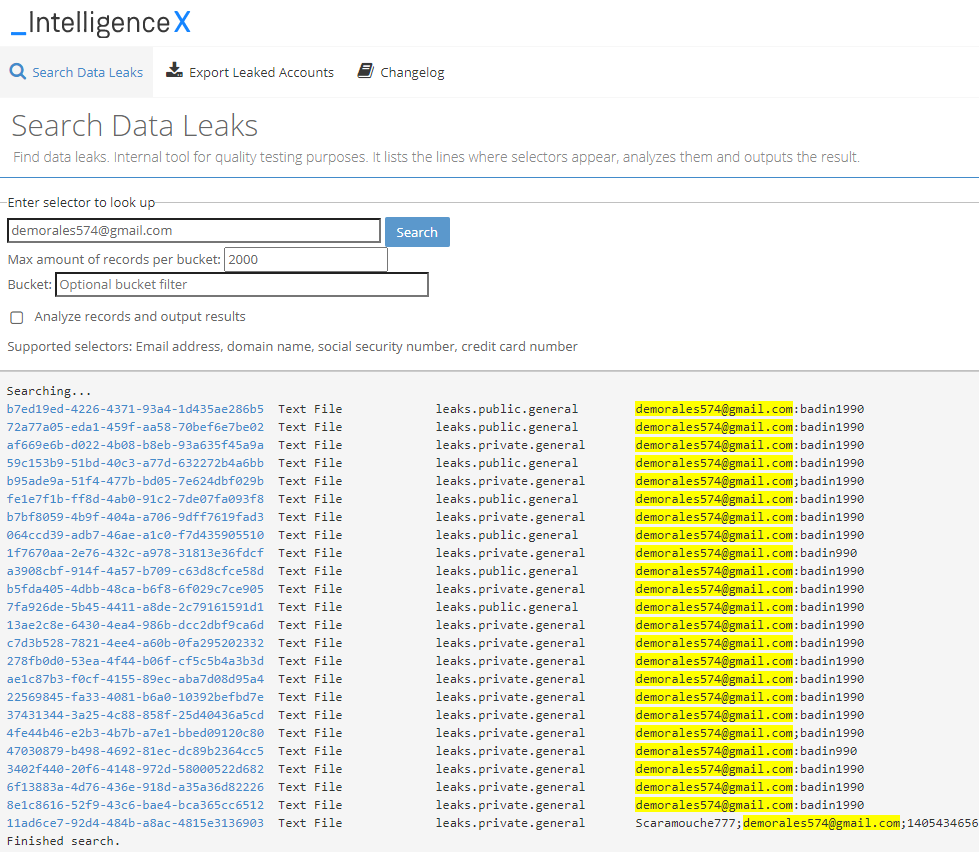
List all lines where the search term appears in the results
This function searches for and lists all lines where a search term appears, and like https://intelx.io/, it searches across all data categories. Each line contains first the ID of the search result, which can be opened by clicking on it. The next columns show the file type and the data category, followed by the line where the search term appears.
This allows analysts to go over hundreds of results and quickly identify duplicates and relevant and irrelevant findings. The screenshots below show the lookup for Dmitry Badin, a supposed GRU member who allegedly hacked the German Bundestag.
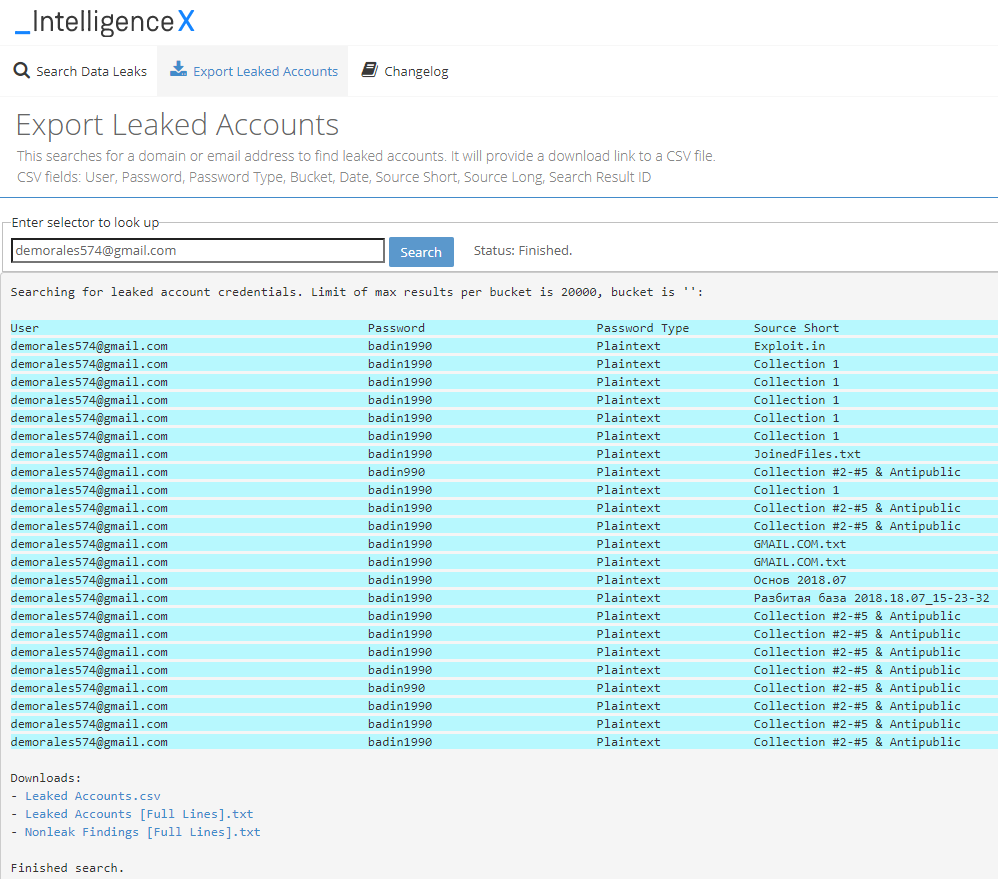
List leaked accounts and export as CSV file
The second tab, “Export Leaked Accounts”, allows users to search for a domain or email and lists all potentially leaked accounts found for a target. It analyzes the password type, including the detection of various hashes, and provides information about the source.
It provides a download link to a CSV file listing all the results. Example CSV file:
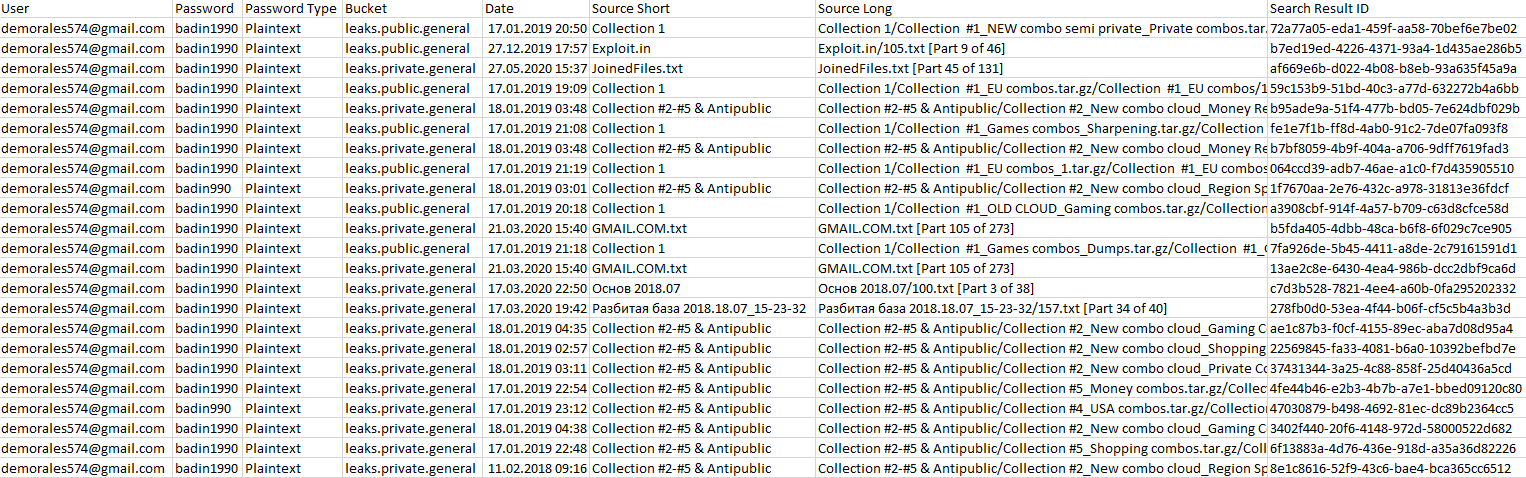
There is a lot of engineering behind both functions since it reads all search results data in real-time, converts them to text, and analyzes the result to determine whether it is a leaked account. Given that Intelligence X searches more than 200 billion records, this can result in Gigabytes of data being processed for a single request.
Search for Selectors
- Email address
- Domain, including wildcards like *.example.com
- URL
- IP, CIDR. Both IPv4 and IPv6 are fully supported.
- Phone Number
- Bitcoin address
- Ethereum address
- MAC address
- IPFS Hash
- Credit Card Number
- Social Security Number
- IBAN (International Bank Account Number)
- ... and other internal ones like UUID, Storage ID, Simhash
In these categories:
- Paste sites, including historical ones
- Darknet: Tor and I2P
- Wikileaks & Cryptome
- Government sites of North Korea and Russia
- Data Leaks
- Whois Data
- Dumpster: Everything else
- Public Web